The OSI layers model was developed to ensure network device (and operating system) compatibility regardless of manufacturer. The International Standard Organisation describes OSI as “Open Systems Interconnection” (ISO).
The OSI layers model was created to make interoperability between vendors easier and to establish consistent network communication standards. The older TCP/IP model, on the other hand, is still the most widely used reference system for Internet communications today.
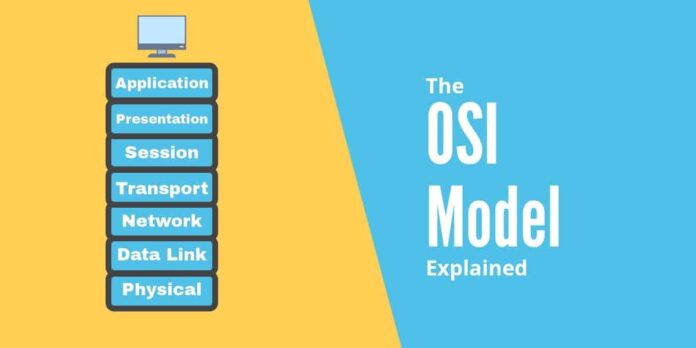
The seven OSI layers relate to the Open Systems Interconnection (OSI) model, which is a conceptual paradigm that defines the functions of a networking or telecommunication system for IT professionals.
The model is made up of seven OSI layers:
- Application layer
- Presentation layer
- System layer
- Transport layer
- Network layer
- Data layer
- Physical layer
Which of the following mnemonics can be used to remember: The 7 OSI layers are depicted in detail in the diagram below.
The Host OSI Layers
The model’s first four OSI layers work at the operating system/software level inside the host:
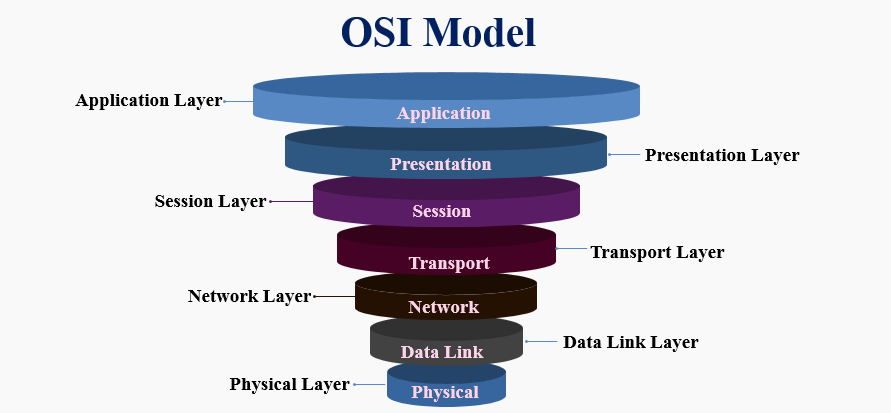
Application Layer
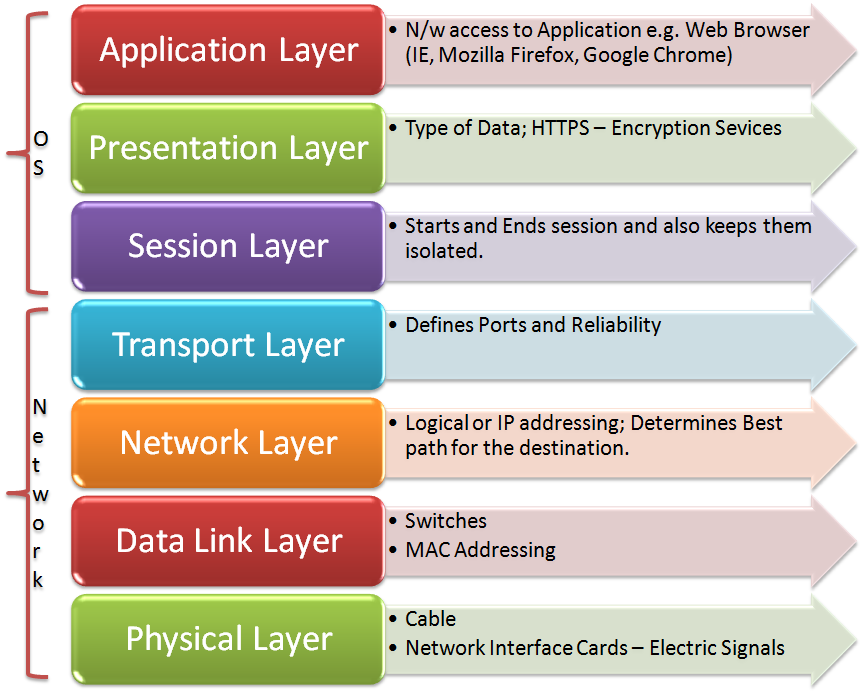
The application layer was a little perplexing to me because it doesn’t affect application programs per se, but rather allows applications to access network resources by providing an interface to the layers below it. Its main concern is ensuring that other hosts in the network have the tools they need to communicate. It coordinates collaborating applications and guarantees data integrity and error recovery procedures. The application layer is only activated when it is clear that network access will be needed soon.
Presentation Layer
The data is presented to the application layer by the presentation layer. It’s in charge of preparing data for transmission by encoding and decoding it. The format of data is specified by the norm. This layer is responsible for data compression, decompression, encryption, and decryption.
Session Layer
The session layer is in charge of ensuring that network requests from applications are sent only to and from that application. It prevents data from being exchanged with other requesting applications on the same server. It accomplishes this by establishing, maintaining, and terminating a session for each network application request. It also coordinates communication between systems and decides whether the transmission will be simplex, half-duplex, or full-duplex (as discussed in data communication fundamentals).
Transport Layer
The transport layer is in charge of bringing data into a data stream and sending it out onto the network from the host. The Transmission Control Protocol (TCP) and the lesser-known UDP (User Datagram Protocol) both operate in this area.
They are the laws that govern how data is sent from one host to another. TCP ensures that a stream of bytes is transmitted in a secure, orderly, and error-checked manner between applications operating on hosts, while UDP is much more lenient when it comes to data stream reliability. UDP is a connectionless protocol that doesn’t mind if the link fails and prioritizes latency over reliability.
The Layers of Media
The media layers are the next three layers, and they are responsible for actually transferring data between hosts, beginning with the:
The network layer is responsible for determining the location of devices on a network in order to determine the path that data would take through the network to get from the sender to the receiver. Routers are used to handle logical device addressing (IP addresses) at the network layer.
Network Layer
User data is transported over the internet using Data Packets. Routed protocols are protocols that support data traffic. Internet Protocol (IP) and Internet Protocol version 6 (IPv6) are two examples of routed protocols (which will be discussed next week, so stay tuned!).
Route-Update Packets are used to inform nearby routers about the networks that are linked to all routers in the internetwork. Routing protocols are those that send route-update packets, and the Routing Information Protocol (RIP), RIPv2, Enhanced Interior Gateway Routing Protocol (EIGRP), and Open Shortest Path First are a few examples (OSPF). Route-update packets are used to help each router create and manage routing tables.
Data Link Layer
The Data Link layer manages error notification, network topology, and flow control in addition to providing physical data transmission. This means that the Data Link layer uses hardware (MAC) addresses to ensure that messages are sent to the correct computer on a LAN, and it converts messages from the Network layer into bits for the Physical layer to transmit.
To proceed with our Birmingham-to-Plymouth letter analogy. The router is aware that the letter must be sent to a Plymouth address. The data link layer devices are aware of the exact address in Plymouth where the letter should be sent.
The Data Link layer breaks down the message into data frames and adds a custom header with the destination and source hardware (MAC) addresses. This additional data forms a kind of capsule around the original post, ensuring that once it has passed through the internetwork to a rough spot, the devices in the data link layer have enough information to ensure it arrives at the precise destination.
Physical Layer
The Physical layer performs two essential functions: it sends and receives bits, as well as communicating directly with different types of actual communication media. These bit values are represented in a variety of ways by various types of media.
Others use state transitions—voltage shifts from high to low and low to high—while others use audio tones (bring back 56k modems, please!). To explain the proper bit patterns to be used, how data is encoded into media signals, and the various qualities of the physical media’s attachment interface, such as electrical, mechanical, procedural, and functional specifications for enabling, maintaining, and deactivating a physical link between end systems, specific protocols are required for each form of media.
The OSI Model’s Advantages
The following are some of the main advantages and disadvantages of using the OSI layers model:
- It aids in the standardization of router, switch, motherboard, and other hardware
- It reduces complexity and standardizes interfaces.
- It facilitates modular engineering.
- It aids in the development of interoperable technology.
- As technology advances, old protocols may be replaced by new protocols.
- It is a common model of computer networking that supports both connection-oriented and connectionless services.
- Allows for both connectionless and connection-oriented services to be used.
- Allows for adaptability to a variety of protocols.
The OSI Model’s Disadvantages
The following are some disadvantages of using the OSI layers Model:
- Fitting protocols is a time-consuming process.
- It can only be used as a model for comparison.
- No particular protocol is described.
- Certain services are duplicated in several layers of the OSI network layer model, such as the transport and data link layers.
- OSI layers are unable to operate in parallel since each layer must wait for data from the previous layer.